Why Risk Management in GDPR Is Important - and How to Do It Step-By-Step
- May 2, 2024

Risk management is a critical part of your GDPR compliance. Limiting risk to data subjects is a responsibility all organizations share.
But to many, managing and limiting risks feels like driving to work in rush hour:
Overwhelming. And even the smallest progress takes forever.
It doesn’t have to be like that. The most important thing is that you do the best you can in structuring and prioritizing your efforts.
And after reading this blog post, you’ll know how you do that as we give you the answers to:
What is risk management?
Risk management is about identifying and dealing with potential threats according to relevant laws or frameworks.
These threats can pop up from anywhere and often show themselves as financial risks, legal risks, strategic risks, accidents, or even natural disasters.
When looking from a GDPR perspective, the severity is always determined by the risk it poses to the data subject.
Why is risk management of assets important?
It’s important to assess your risks, so you know how to put up the right security controls (also called security measures) and, by that, can mitigate them.
Risk management in GDPR is important because you must protect users’ personal data and right to privacy. And you can only do this if you have the proper security on your assets.
An asset is anything, tangible or intangible, that could cause harm if subject to a threat.
Common examples of assets are IT systems, processing activities, devices such as mobile phones or computers, data, and office Wi-Fi networks.
Besides the primary reason above, risk management is also important because you:
- Comply with the GDPR and, thereby, avoid fines and penalties
- Ensure a good reputation
- Protect and strengthen customer trust
There are many approaches an organization can follow when conducting risk assessments, and there’s no comprehensive checklist.
However, we suggest that you use ISO 27005. It’s an international standard for helping organizations manage their information security, cybersecurity, and privacy protection.
This is also the standard that our 5 steps-approach in doing risk assessment is based on.

5 steps in risk assessing your assets
We recommend this 5 step-approach when you do a risk assessment of your assets:
- Identify and prioritize your assets
- Identify potential threats
- Assess the likelihood and consequence of threats
- Describe security and reassess risk score
- Review regularly and update security
Step 1: Identify and prioritize your assets
First and foremost, you should identify threats to be able to deal with relevant and/or potential risks.
This means the risk of processing specific data.
This first step can seem overwhelming. Especially, if you’re in a company that has a lot of assets.
To overcome this challenge, we advise you to do a preliminary evaluation of your assets. You can do this by making a rough estimate on the consequence and likelihood of the worst-case scenario for a given asset.
For example:
If a particular IT system is not used for processing any personal data, the estimated consequence of a data breach will likely be low.
On the other hand, if you use an IT system for processing sensitive data, the estimated consequence of a data breach will likely be severe.
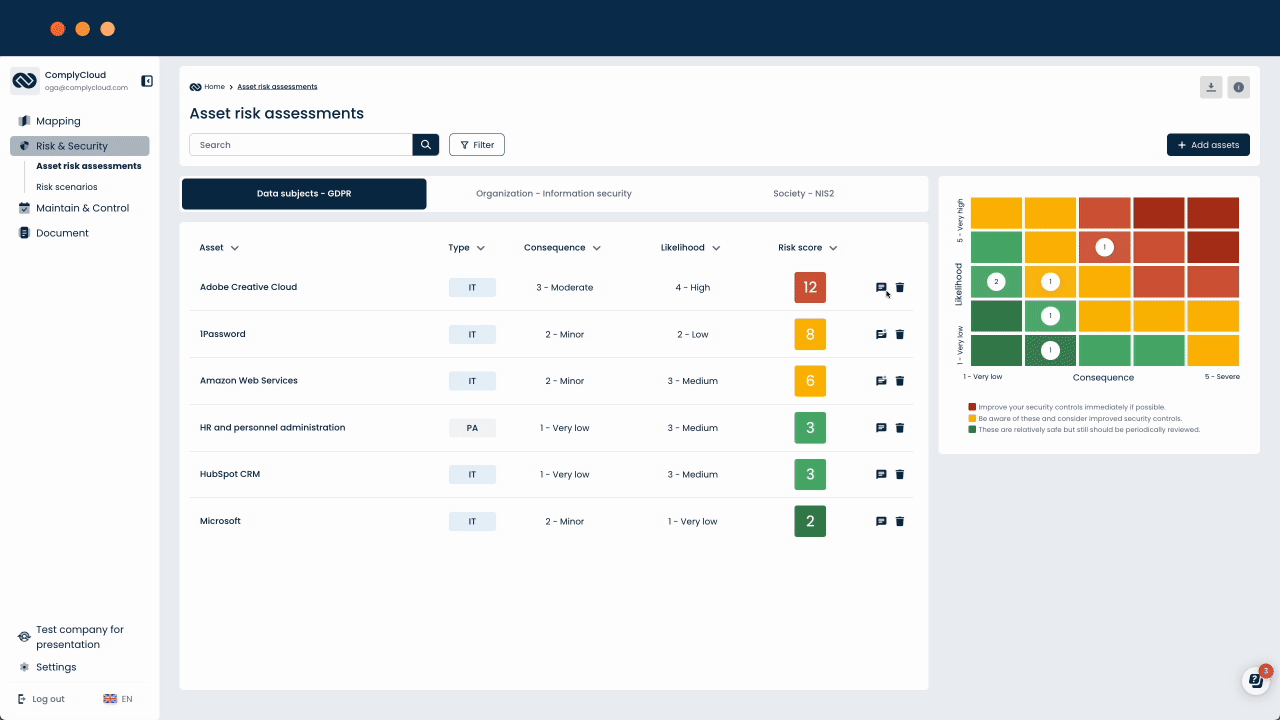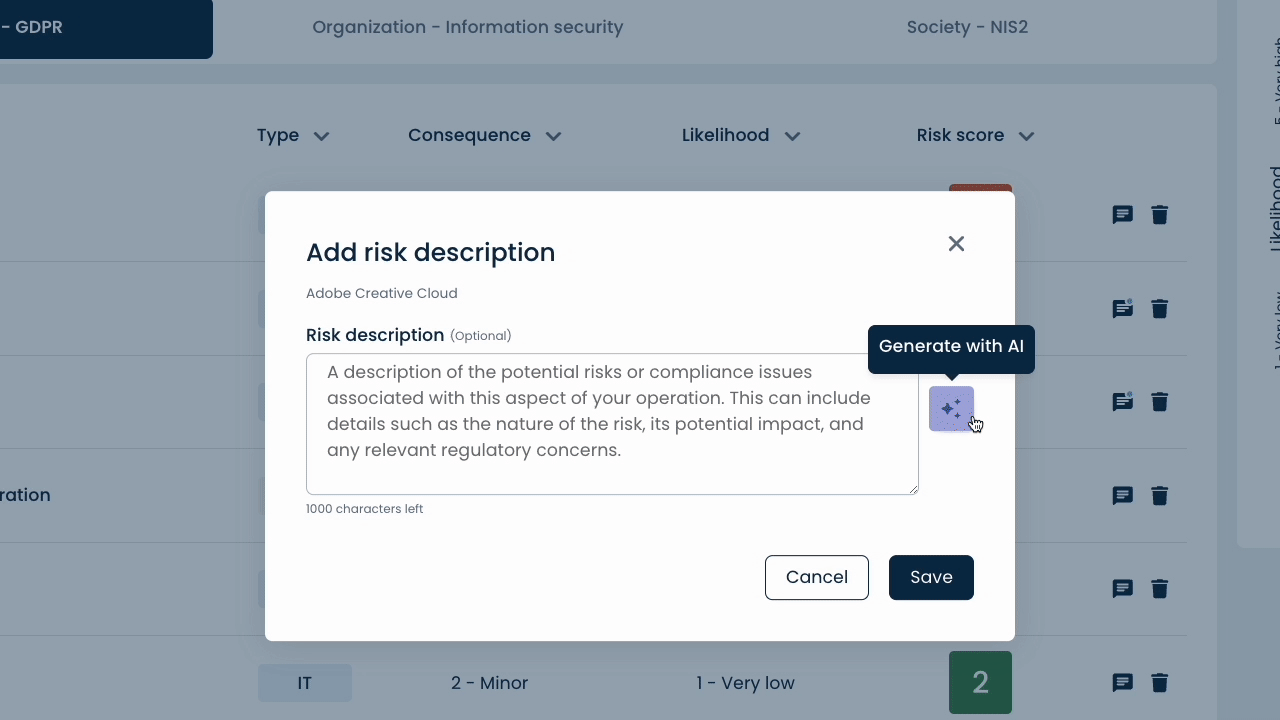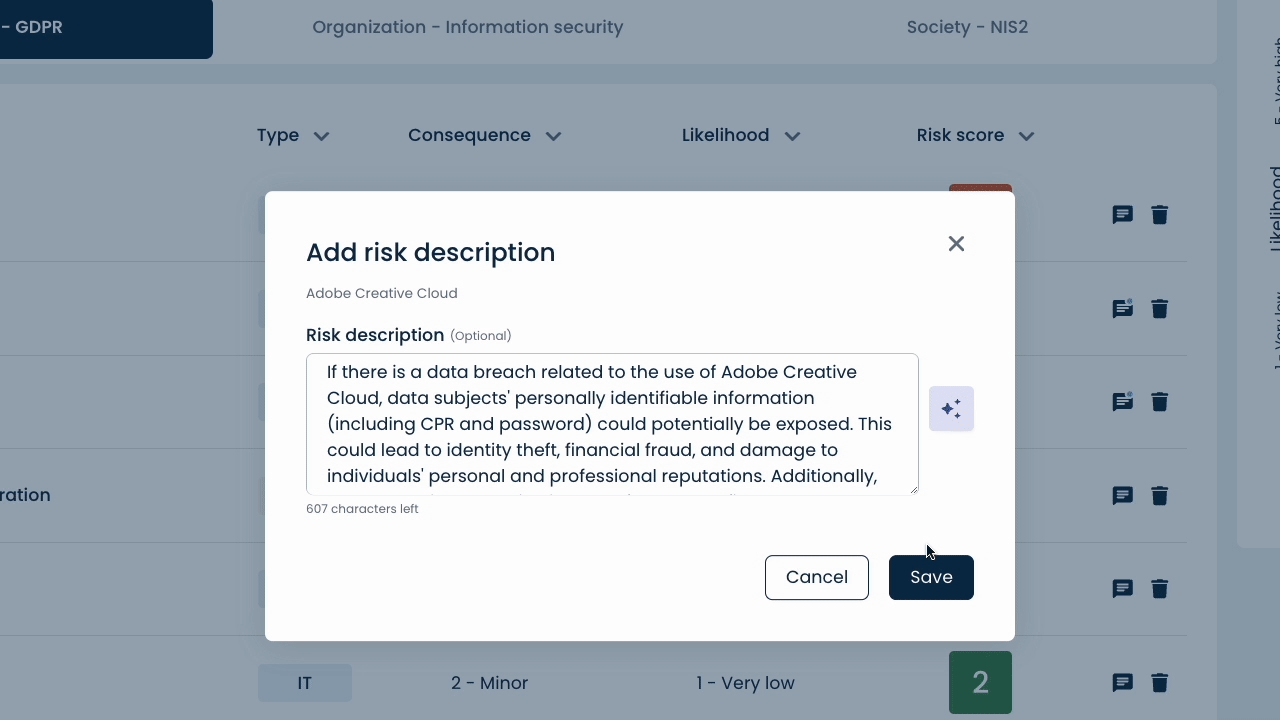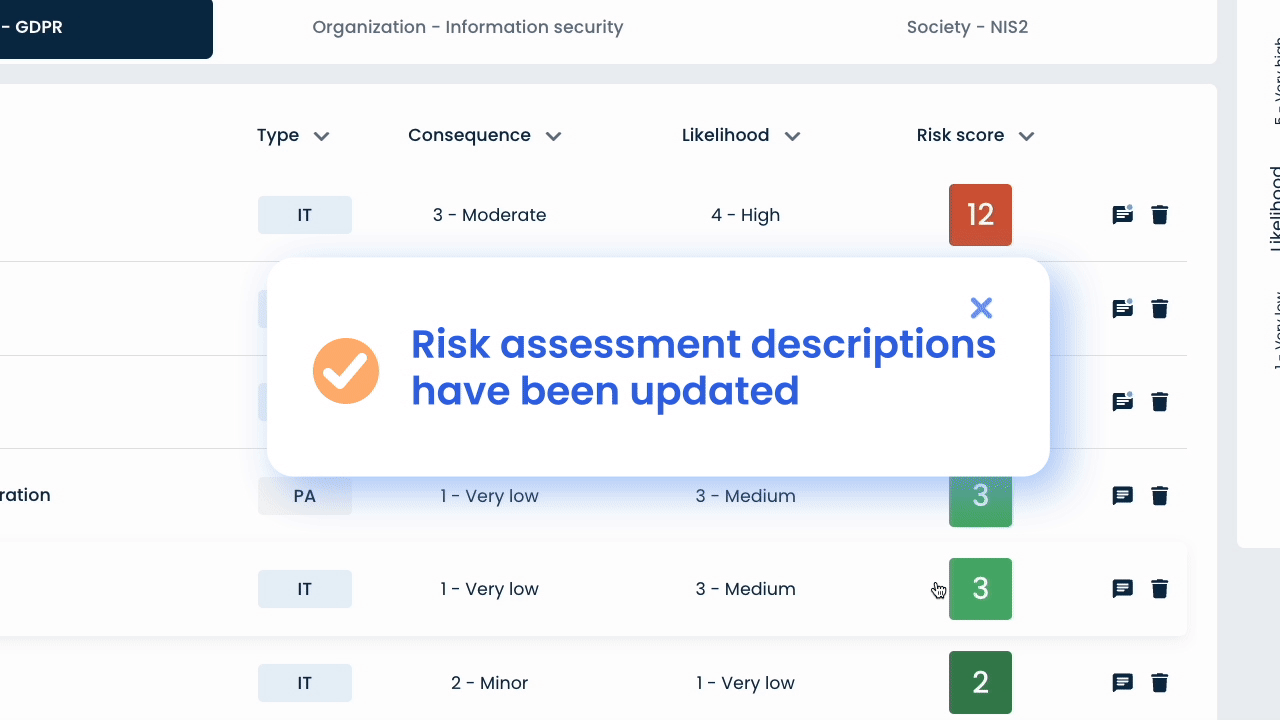
If the likelihood of that to happen is high, your asset will come with a high risk – and, by that, place itself in the red area in the risk score below:

When you’ve done a rough estimate on all your assets, you have an overview of your high-risk assets.
Having this overview, you now have what you need to follow the 80/20 rule and answer this question:
Which 20% of my IT systems can account for the 80% of the risks that I need to protect my data subjects against?
Then you should start your risk assessment on these 20%. You can argue why you prioritize certain assets, suppliers, and IT systems over others in your risk assessments.
Step 2: Identify potential threats
As the next step, you assess the likelihood of a threat happening in reality. In this case, you need to consider several aspects. These include the so-called capabilities of the threat.
For instance:
The likelihood of your organization falling victim to hackers will depend on the motivation and skill level of people who may target you.
If your organization is likely to be targeted by a nation-state who commits many resources to cyber-attacks, the likelihood should be greater than if the potential hackers acting as individuals.
Step 3: Assess the likelihood and consequence of threats
As the next step, you should assess the consequence and likelihood of each threat related to your asset. So, just as you assessed the overall risk of each asset in step 1, you now need to do the same process but for each threat related to your assets.
If a hacker attack causes a data breach, you should assess the consequences for the data subject. In other words: what it means if the personal data processed about them loses its confidentiality, availability and/or integrity.
When you’ve assessed the consequences and likelihoods of all your threats, you might have an overview like this:

The threats in the green areas are overall safe.
However, you need to be aware of the threats in the yellow areas and consider better security controls.
Finally, the threats in the red areas needs your attention right away and you need to ensure the best possible security controls as soon as possible. And this leads us to the next step.
Step 4: Describe security controls and reassess risk score
The fourth step is about describing your security and reassessing your risk score.
Describing security on a threat can involve existing security controls and the ones you plan to implement to mitigate risk.
It can be security controls that can hinder a hacker from gaining access to your systems and that you mitigate the risk by, for instance, ensuring encryption, regular software updates, or awareness and training of employees.
When you’ve described and implemented your security measures, you’ve lowered the risk level as much as possible.
However, you’ll be left with a so-called residual risk. Whether this risk level is acceptable, depends on your specific organization, industry, and so on.
In any case, your residual risk shows the effectiveness of your existing and implemented security controls.
These should be clear in the risk score when you reassess it, by having moved the threats to the green/safer areas:

If you still find some threats in the red area, you should reconsider your security controls on these, by, for instance, asking yourself if you should choose another system, or find an additional system that mitigate the risk.
Step 5: Review regularly and update security
Like any other part of your compliance work, risk management is an ongoing thing.
For instance, when your business is growing, you’ll naturally process data of more people since you get more employees and more customers.
The consequence of a data breach of 2,000 people’s personal data is more severe compared to a data breach that ‘only’ involves 100 people.
Other reasons for you to do risk management and ensure constant compliance are that new technologies are invented, meaning that the way you process data also changes. Also, hackers get ‘better and better’, and the threat landscape changes, meaning that your systems and security measures also need to be better.
After reviewing your threats, you, of course, have to update your security measures to mitigate your risks.
How do to your risk management with minimal time and effort
Whether we talk to customers who are ‘green’ or experienced in GDPR, they all face the same challenge when it comes to risk management:
It takes time.
Because you almost have to reinvent the wheel when describing your risks. It’s tricky to find out what’s the ‘right’ way to do it and when a description is adequate.
If you want to limit the time and money you spend on that part, we might have the right solution for you:
ComplyCloud AI – the only tool to offer AI-powered suggestions for risk assessments.
This means that ComplyCloud AI helps you automate the descriptions of risks, threats, and security controls in your company – and gives you the confidence in conducting accurate risk assessments.